Infographic Protecting Patient Data
•
3 recomendaciones•6,647 vistas
Learn the security risks of digital healthcare technology and how healthcare organizations can protect their patients’ data with Fortinet’s Security Fabric.
Denunciar
Compartir
Denunciar
Compartir
Descargar para leer sin conexión
Recomendados
Recomendados
High Performance Medical Reconstruction Using Stream Programming Paradigms

High Performance Medical Reconstruction Using Stream Programming ParadigmsQuEST Global (erstwhile NeST Software)
How marketers can leverage Ektron DXH's Exact Target for better client engage...

How marketers can leverage Ektron DXH's Exact Target for better client engage...Suyati Technologies Pvt Ltd
Más contenido relacionado
Destacado
High Performance Medical Reconstruction Using Stream Programming Paradigms

High Performance Medical Reconstruction Using Stream Programming ParadigmsQuEST Global (erstwhile NeST Software)
How marketers can leverage Ektron DXH's Exact Target for better client engage...

How marketers can leverage Ektron DXH's Exact Target for better client engage...Suyati Technologies Pvt Ltd
Destacado (18)
Cloud Expo May 09 Richard Britton, Cloud Computing for SMEs

Cloud Expo May 09 Richard Britton, Cloud Computing for SMEs
Data on demand flexible archiving in a big content world

Data on demand flexible archiving in a big content world
High Performance Medical Reconstruction Using Stream Programming Paradigms

High Performance Medical Reconstruction Using Stream Programming Paradigms
Insperity Business Confidence Survey Q2 2015 [Infographic]![Insperity Business Confidence Survey Q2 2015 [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Insperity Business Confidence Survey Q2 2015 [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Insperity Business Confidence Survey Q2 2015 [Infographic]
iBOS Solution - Incessant Business Operations Suite 

iBOS Solution - Incessant Business Operations Suite
Call Management Services Should be Part of Every Business Telephone System

Call Management Services Should be Part of Every Business Telephone System
How marketers can leverage Ektron DXH's Exact Target for better client engage...

How marketers can leverage Ektron DXH's Exact Target for better client engage...
Similar a Infographic Protecting Patient Data
Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...

Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...The Lifesciences Magazine
Similar a Infographic Protecting Patient Data (20)
Systems Thinking on a National Level, Part 2Drew David.docx

Systems Thinking on a National Level, Part 2Drew David.docx
Why healthcare is the biggest target for cyberattacks-converted.pdf

Why healthcare is the biggest target for cyberattacks-converted.pdf
[Infographic] 5 Security Threats in Healthcare Industry ![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] 5 Security Threats in Healthcare Industry](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] 5 Security Threats in Healthcare Industry
Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...

Best 3 Cyber Threats in Healthcare Organizations Today | The Lifesciences Mag...
Cybersecurity Challenges in the Healthcare Industry.pdf

Cybersecurity Challenges in the Healthcare Industry.pdf
Más de Fortinet
Más de Fortinet (12)
Fortinet's Secure SD-WAN: Gartner Peer Insights Reviews

Fortinet's Secure SD-WAN: Gartner Peer Insights Reviews
Why Partners Who Charge for Technical Assessments Have Higher Growth and Profit

Why Partners Who Charge for Technical Assessments Have Higher Growth and Profit
The Importance of Targeting your Customers - Cross Selling Execution

The Importance of Targeting your Customers - Cross Selling Execution
Infographic: Bringing Your Cloud Visibility Back Into Focus

Infographic: Bringing Your Cloud Visibility Back Into Focus
Infographic: Fortinet Q1 2017 Threat Landscape Report

Infographic: Fortinet Q1 2017 Threat Landscape Report
Último
Importance of Assessing Level of Consciousness in Medical Care | The Lifescie...

Importance of Assessing Level of Consciousness in Medical Care | The Lifescie...The Lifesciences Magazine
Último (20)
Medisep insurance policy , new kerala government insurance policy for govrnm...

Medisep insurance policy , new kerala government insurance policy for govrnm...
DELIRIUM psychiatric delirium is a organic mental disorder

DELIRIUM psychiatric delirium is a organic mental disorder
Lipid Profile test & Cardiac Markers for MBBS, Lab. Med. and Nursing.pptx

Lipid Profile test & Cardiac Markers for MBBS, Lab. Med. and Nursing.pptx
Learn Tips for Managing Chemobrain or Mental Fogginess

Learn Tips for Managing Chemobrain or Mental Fogginess
Dr Sujit Chatterjee Hiranandani Hospital Kidney.pdf

Dr Sujit Chatterjee Hiranandani Hospital Kidney.pdf
Mental Health for physiotherapy and other health students

Mental Health for physiotherapy and other health students
Artificial Intelligence Robotics & Computational Fluid Dynamics

Artificial Intelligence Robotics & Computational Fluid Dynamics
Importance of Assessing Level of Consciousness in Medical Care | The Lifescie...

Importance of Assessing Level of Consciousness in Medical Care | The Lifescie...
Leading big change: what does it take to deliver at large scale?

Leading big change: what does it take to deliver at large scale?
EMS Response to Terrorism involving Weapons of Mass Destruction

EMS Response to Terrorism involving Weapons of Mass Destruction
Professional Ear Wax Cleaning Services for Your Home

Professional Ear Wax Cleaning Services for Your Home
Back care and back massage. powerpoint presentation

Back care and back massage. powerpoint presentation
Infographic Protecting Patient Data
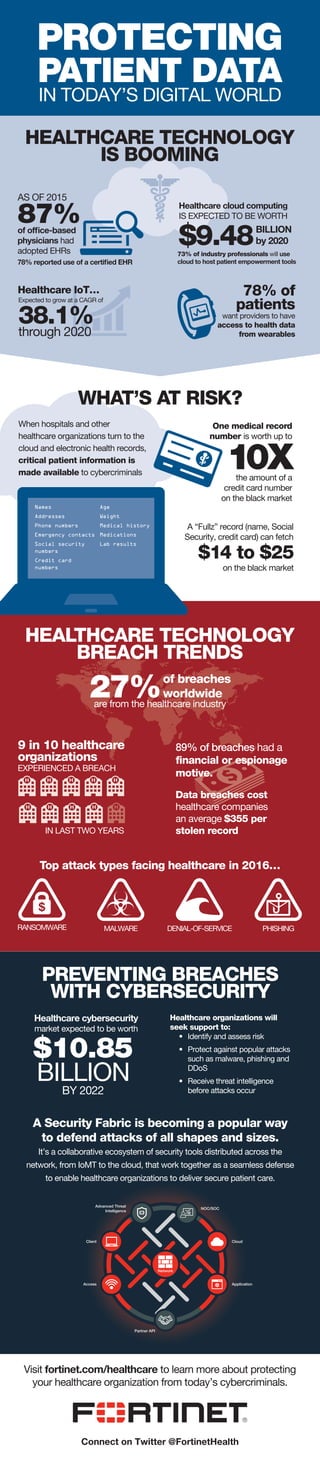
- 1. PROTECTING PATIENT DATA IN TODAY’S DIGITAL WORLD HEALTHCARE TECHNOLOGY IS BOOMING WHAT’S AT RISK? PREVENTING BREACHES WITH CYBERSECURITY HEALTHCARE TECHNOLOGY BREACH TRENDS When hospitals and other healthcare organizations turn to the cloud and electronic health records, critical patient information is made available to cybercriminals One medical record number is worth up to A “Fullz” record (name, Social Security, credit card) can fetch 89% of breaches had a financial or espionage motive. Top attack types facing healthcare in 2016… Data breaches cost healthcare companies an average $355 per stolen record Healthcare cybersecurity market expected to be worth Healthcare organizations will seek support to: • Identify and assess risk • Protect against popular attacks such as malware, phishing and DDoS • Receive threat intelligence before attacks occur A Security Fabric is becoming a popular way to defend attacks of all shapes and sizes. It’s a collaborative ecosystem of security tools distributed across the network, from IoMT to the cloud, that work together as a seamless defense to enable healthcare organizations to deliver secure patient care. Visit fortinet.com/healthcare to learn more about protecting your healthcare organization from today’s cybercriminals. AS OF 2015 87%of office-based physicians had adopted EHRs 78% reported use of a certified EHR Healthcare cloud computing IS EXPECTED TO BE WORTH BILLION by 2020 73% of industry professionals will use cloud to host patient empowerment tools $9.48 Healthcare IoT… Expected to grow at a CAGR of 38.1%through 2020 78% of patients want providers to have access to health data from wearables 10Xthe amount of a credit card number on the black market $14 to $25 on the black market Names Addresses Phone numbers Emergency contacts Social security numbers Credit card numbers Age Weight Medical history Medications Lab results 9 in 10 healthcare organizations EXPERIENCED A BREACH IN LAST TWO YEARS RANSOMWARE MALWARE DENIAL-OF-SERVICE PHISHING $10.85 BILLION BY 2022 NOC/SOC Cloud Partner API Access Client Advanced Threat Intelligence Application Network 27%are from the healthcare industry of breaches worldwide Connect on Twitter @FortinetHealth
